What is a Zero Trust security model?
If you’ve worked in the IT industry long enough, you’ll no doubt have seen various models and methodologies covering a wide range of technology sets.
Zero Trust is at the core of an IT security framework that covers the following key concepts:
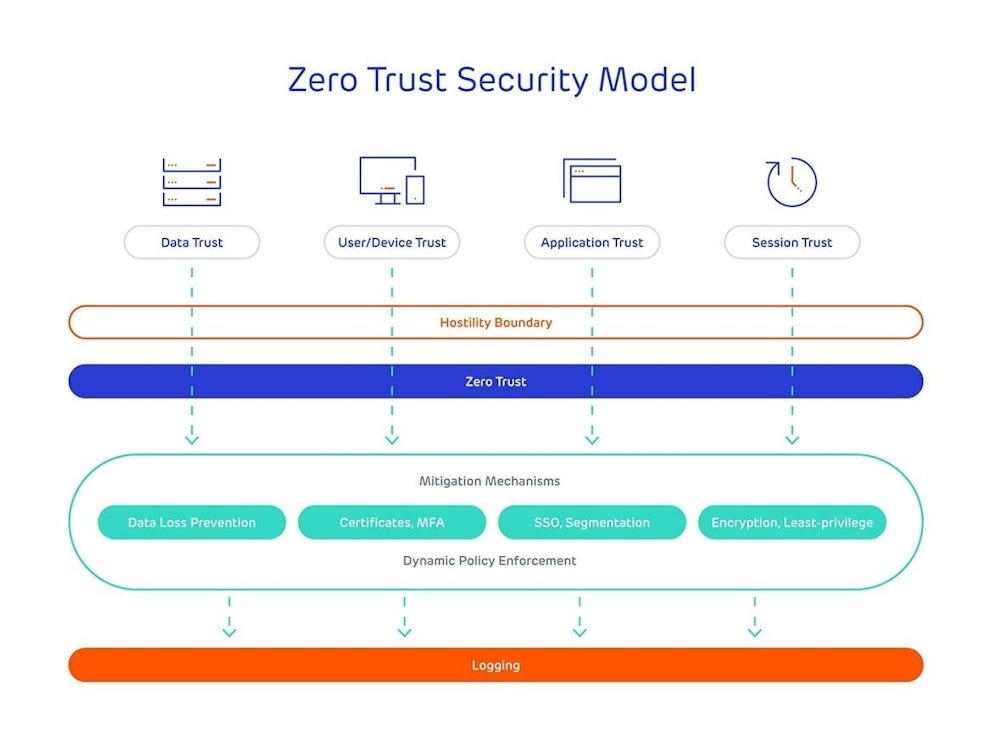
Of course, there are many moving parts here. But the key concept to take away from this diagram is that each part of the Zero Trust model works in unison to provide the protection businesses require in the Information Age.
According to the 2020 Verizon Data Breach Investigations Report 86% of breaches analysed were financially motivated and 58% of victims had personal data compromised. What is also concerning is that ‘since 2017, Misconfiguration errors have been increasing. This can be, in large part, associated with internet-exposed storage discovered by security researchers and unrelated third parties. In part - due to the increase in cloud usage and remote working - we need to understand and protect our data. The methods we used previously are no longer sufficient.
Who created Zero Trust?
The term Zero Trust was coined in 2010 by Forrester Research Inc. Prior to this, in 2009, Google suffered a breach which resulted in the loss of intellectual property (IP). Google understood that the traditional enterprise security model was problematic and developed its own Zero Trust model – BeyondCorp.
The attack against Google was part of Operation Aurora, a series of Cyber-attacks conducted by advanced persistent threats. Google described the attack as ‘a "highly sophisticated" and coordinated hack attack against its corporate network.’ Google also stated that ‘hackers had stolen intellectual property and sought access to the Gmail accounts’ and that ‘the attackers used nearly a dozen pieces of malware and several levels of encryption to burrow deeply into the bowels of company networks and obscure their activity’
Google’s focus on Zero Trust provided the impetus required to bring this approach to the modern enterprise. In 2019, Gartner understood that the future is in the ‘cloud’ and coined the term secure access service edge (SASE).
What is Secure Access Service Edge?
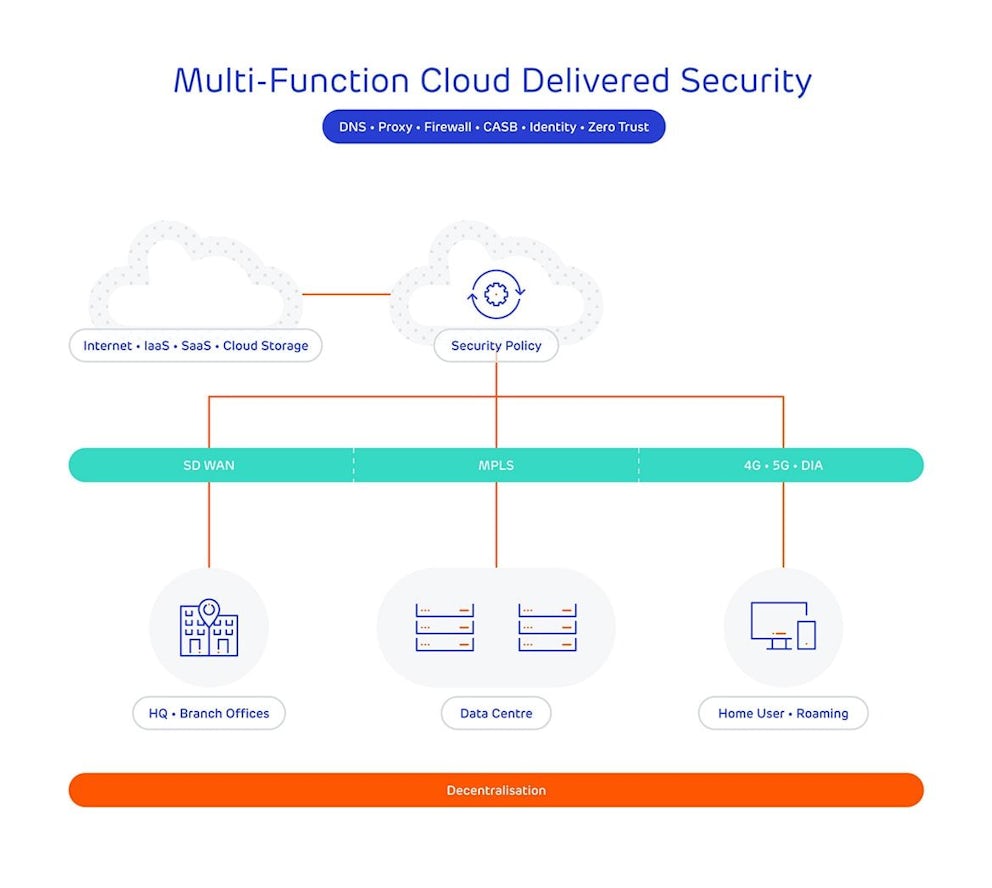
Secure access service edge (SASE) is the unification of Zero Trust security and Wide area network (WAN) capabilities to support dynamic, secure access. With the explosive growth of public cloud apps and services, more and more data is being stored outside of the traditional network boundaries. In the 2019 ‘The Rise of Direct Internet Access’ report by ESG, 60% of respondents claim that SaaS applications will account for 50% or more of their organisations business applications by 2021 and that 48% of European workers will be considered remote users in the same timeframe.
With the decentralisation of the mechanisms we use to connect to our data, the common point of access is the cloud itself and traditional security enforcement points are no longer sufficient. SASE (pronounced ‘sassy’) is an approach to securing this distributed access outside of the traditional network perimeter. The SASE security cloud sits between the users and cloud services, providing all the controls and capabilities required.
Why do modern organisations need to consider implementing a Zero Trust Security approach?
New threats are continually emerging, and existing threats are evolving. These threats can come from a variety of sources, both internally and externally.
The approach of protecting your business at the boundary no longer provides sufficient protection in today’s threat landscape. If you head off on holiday and leave your car in long-term parking, you feel content in the knowledge it’s safe. You’ve closed the windows, locked the doors and put all your valuables out of sight.
Zero Trust extends to all parts of the enterprise security strategy, so we need to ensure a holistic approach is taken to ensure end to end protection. This will range from the network itself, applications, data access and more.
But would you feel quite as content if you’d locked the doors but left the windows open and the keys in the ignition?
The 2019 Zero Trust Adoption Report from Cybersecurity Insiders states that 78% of respondents are looking to adopt zero trust and 15% already have. The report also states that 47% lack confidence in their existing technology, with 37% saying that their number 1 user case is securing access to multi-cloud environments
How do you achieve Zero Trust?
Achieving Zero Trust is a multi-stage process involving several teams. In this section, we’ll discuss the key steps your business needs to take.
Stakeholder engagement
The first step in the path to Zero Trust is crucial. Without the support of your key stakeholders, promoting the shift to a Zero Trust environment will be extremely difficult. Therefore, it’s important to outline the business benefits and the critical goals of the Zero Trust Security Model to align teams and strategy. Your applications may have been developed in house or evolved over time and may not have the required security controls inbuilt. Discovering these limitations can lead to further considerations – is it more secure to move to a cloud-based SaaS architecture or utilise VDI solutions?
Discovery & inventory
Zero Trust is not only focused on the security teams. There’s going to be a lot of input from several departments within the business. So, you must have full visibility into all the moving parts required. After all, you cannot protect what you cannot see or have no knowledge of. Understanding the devices, applications, flows and permissions in your existing estate will go a long way towards improving your network security.
Design & policy creation
With stakeholder buy-in and a full inventory of your existing estate, you can now begin to create the overall design that will lead you to implement Zero Trust. Be prepared, it’s going to be a large piece of work with input from several teams. Each section of the design requires careful consideration, giving specific attention to the potential impact that each component will have on one another.
Within the design, it will be essential to understand and call out the new components required for the shift to Zero Trust. Examples are identity management, multi-factor authentication (MFA), segmentation, encryption, SSO, certificates as shown below:
- User authentication = ‘Passwordless’, MFA, Biometric, Certificates
- Devices = Integrity, compliance
- Applications = Additional development to increase security, ‘VPNless’ access, work to retire legacy apps
- Data = Data Access method & Policies
- Network = Group and microsegment with policy
If you don’t have the technologies required, consider engaging with vendors who offer the solutions and can help you understand them fully. Within the design, keep a focus on integration and avoid the use of standalone, disparate solutions that increase the workload of relevant support staff and decrease the efficacy of the data produced.
Lab environment testing
Where possible, all solutions should be thoroughly tested in a lab environment before any production rollout. The key to lab testing is to have a representative environment that mimics your production environment as closely as possible. Build out the components required for Zero Trust and have a detailed plan in place to test all possible scenarios. It’s important to understand what the business impact would be if one part of the Zero Trust architecture fails – will this mean users cannot access the resources they require and what mitigations are in place for this? Use the lab testing to make informed design decisions and revise the overall design if needed. If the design is modified, test some more.
Phased testing deployment
Only once full lab testing has been completed and design decisions have been taken, can you then move on to the phased deployment of the Zero Trust Security Model. New hardware, and applications can stand up during this phase and key test users should be selected. The critical test users will need to undertake training on the use and impact of the new solution and have a clear reporting structure to record any issues.
The tests-users must make use of their machines and applications as they would on a typical business day. You can then use the feedback from this initial phased deployment to fine-tune the solution and iron out any issues. Once you’ve completed this, you can move on to phase two of the testing and bring in more users.
Full review of the phased deployments
Once the phased deployment stages are complete, you need to take time to review all the results. You should understand any design decisions that were taken as part of the testing process and create a plan for the production rollout based on these results.
Business communication & user training
Manage your business expectations by ensuring that key stakeholders are aware of the progress at every stage. Before the production rollout, we recommend having a detailed, structured plan in place, as well as back-out strategies and company-approved timescales.
As with phased testing deployment, user training is also vital. Users need to be fully aware of what will change, what the new requirements are, how they report issues and receive the required level of support.
Production rollout
Your production rollout should follow a similar methodology to the phased testing deployment. For example, if you have 50 sites – deploy one at a time and have a clear structure in place to rollout to the least critical locations first. Be sure not to deploy all components of the Zero Trust solution at once. Instead, take the time to rollout individual pieces and gather as much feedback and data as you can. You could stagger the rollout of least privileged access and MFA, begin to bring in some micro-segmentation and network access policy enforcement.
Data gathering
Data gathering is critical to enable a successful Zero Trust deployment. It should take place at all stages of the deployment, so that any issues can be proactively identified and managed to create the best user experience possible. Ensure that what you’re attempting to protect is being protected, and the new measures you’ve put in place have the desired effect.
Our approach to Zero Trust
Here at Forfusion, we focus primarily on the Cisco portfolio of networking and security products, but there is a lot more to a Zero Trust strategy than utilising a single vendor. Within this section we will focus on Cisco, Citrix and Microsoft. Keep an eye out for our new blog posts that will go into further detail on the technologies mentioned in this section. But in the meantime, you can find a brief overview below.
Intent-based Campus Fabric
Cisco Software Defined-Access delivers policy-based automation of users and devices, from the edge to the cloud. Microsegmentation is made possible by the coupling of the SD-Access fabric and Identity Services Engine. You can read our white paper on intent-based Campus Fabrics with Software Defined Access here.
Identity management
Cisco Identity Services Engine (ISE) is a policy management and control platform for wired, wireless and VPN. It supports BYOD, guest access and Cisco TrustSec services. Cisco TrustSec simplifies policy management by providing a unified tag to sessions enabling the ability to provide access based on a tag irrespective of user location, rather than constantly changing IP addresses.
Next generation firewalls
Cisco Firepower Threat Defence (FTD) combines the Cisco ASA and FirePOWER feature sets into one unified image. Traditional ASA features are now complemented by NGIPS, Application Visibility & Control, Advanced Malware Protection, URL and DNS filtering – and much more. Firepower Threat Defence also provides remote access VPN features utilising the AnyConnect client, as well as site-to-site VPN connectivity. It’s all managed through the Firepower Management Centre, a single pane of glass view into your FTD estate.
Endpoint protection
Cisco Advanced Malware Protection is an integrated, intelligence-powered, enterprise-class malware analysis and protection solution. You get comprehensive protection for your organization across the attack continuum: before, during and after an attack.
Multi-factor authentication
Cisco Duo is a user-centric access security platform that provides two-factor authentication, endpoint security, remote access solutions and more.
Network visibility
Cisco Stealthwatch provides enterprise-wide visibility, from the private network to the public cloud. It applies advanced security analytics to detect and respond to threats in real-time. Using a combination of behavioural modelling, machine learning and global threat intelligence, Stealthwatch can quickly and confidently detect threats such as C&C attacks, ransomware, DDoS attacks, illicit crypto mining, unknown malware and insider threats. With a single, agentless solution, you receive comprehensive threat monitoring across your data centre, branch, endpoint, cloud and even encrypted traffic.
Web & email security
Cisco Web Security Appliance (WSA) addresses the need for a corporate web security policy by offering a combination of web usage controls with category and reputation-based control, malware filtering and data protection. Cisco Email Security is your defence against phishing, business email compromise and ransomware. Get threat intelligence updates every three to five minutes through Cisco Talos for the most up-to-date protection.
Data centre
Cisco Application Centric Infrastructure (ACI) is the SDN of the data centre world. Offering a holistic architecture with centralised automation and policy-driven application profiles, ACI delivers software flexibility with the scalability of hardware performance. By using segmentation, Cisco Tetration enables a zero-trust model that offers comprehensive workload protection for multi-cloud data centres.
Cloud security
Cisco Umbrella unifies firewall, secure web gateway, DNS-layer security cloud access security broker (CASB) and threat intelligence solutions into a single cloud service to help businesses of all sizes secure their network. Cisco also offers Cloudlock, featuring data loss prevention (DLP) technology that continuously monitors cloud environments to detect and secure sensitive information. It provides countless out-of-the-box policies, as well as highly tuneable custom policies.
Integration
Cisco SecureX is the broadest, most integrated security platform that connects the breadth of Cisco's integrated security portfolio and the customer's infrastructure for a consistent experience. It unifies visibility, enables automation and strengthens your security across network, endpoints, cloud, and applications - all without replacing your current security infrastructure or layering on new technology.
SaaS Applications
With the continued growth in the SaaS market, it is key to secure not only your network estate but your applications themselves. Focusing on Microsoft Office 365 and Teams, it is clear we need to protect the users & data but also provide policy and monitoring. Microsoft has done a great job of building security into their platforms, but you must ensure the access to the applications and the data available is always appropriate. The benefits of SaaS applications are large and diverse, and if you include them as part of your Zero Trust strategy you should reap the benefits they provide. We can integrate access to O365 and Teams with Cisco Duo, providing MFA, visibility and role-based access control. You can also utilise the Cisco Cloudlock CASB to provide Data Loss Prevention, detect confidential information and detect shadow IT.
Virtual Desktop Infrastructure (VDI)
If your business has made the choice to move to a VDI based architecture utilising Citrix Workspace then you have already taken the first step to simplify management, security and policy. Citrix has several Citrix Ready partners that enhance and complement your Zero Trust security strategy, with one of these being Cisco Duo for MFA and contextual access to resources. Contextual access is key to the Citrix Zero Trust approach, because after all, only allowing users access to the data they require is key to securing your data. Citrix Workspace also employs anti-key logging and screen capture technology, as well as URL filtering. Another important feature in the security of Citrix Workspace is Data Loss Prevention (DLP). With contextual DLP controls you can ensure the safety of your data.Arrange your 30-minute consultation

